How to Hack-proof Asphalt Plant Controls
BY Sandy Lender

In the early 2000s, the chief financial officer for a publishing company based in the Chicago area stored personnel information on a laptop, which was stolen from the headquarters office. Execs felt no need to share the news of the burglary with employees at large.
A few weeks later, employees in satellite locations around the Midwest discovered themselves victims of identity theft; the communications professionals deduced they had a common denominator linking their misfortune and they made accusations. The publishing company’s attorney responded with an internal memo expressing no connection to, and no liability for, identity theft issues.
Thieves have grown more competent at their trade since the early 2000s and, according to NordVPN Teams, the construction industry is a tasty cybercrime target. They report “68 percent of construction executives have no cybersecurity measures in place.”
Just as there are myriad ways for cybercriminals to access heavy equipment on the connected jobsite, data in the control house and sensitive information from the central office, there are myriad ways to block them. Let’s see how to protect your asphalt business and hack-proof your plant controls.
Cybercrime Grows for Asphalt Operations
Consider first the building information modeling (BIM) central database used by the prime contractor for a highway project. Using devices and construction tools that are connected, multiple workers can update BIM in real-time.
This is efficient.
This is also rife with exposure.
While improving communication and efficiency, the high number of end-point devices means sensitive information is exposed all over the project, all over a system that should act like a virtual private network (VPN).
Cisco.com defines the VPN as “an encrypted connection over the internet from a device to a network. The encrypted connection helps ensure that sensitive data is safely transmitted. It prevents unauthorized people from eavesdropping on the traffic and allows the user to conduct work remotely.”
Juta Gurinaviciute, the chief technology officer for NordVPN Teams, shared: “The construction industry is heavily interconnected.” She used the example of vertical construction, but the concept applies to any complex project or production facility with multiple customers, as we’ll discuss in the “Get Specific with Customer Access” portion of this article.
“Several building sites need to exchange data with headquarters and routinely access cloud services,” Gurinaviciute said. “Most workers use laptops and other end-point devices, with architects, engineers and sub-contractors contributing online.”
As Gurinaviciute pointed out, the construction industry isn’t just manual labor anymore. It’s a sophisticated and digitally-managed trade, using high-end innovations and tools alongside our skilled laborers. Data breaches within the industry primarily affect company processes, resulting in prolonged downtime and operational disruption.
Larson Electronics’ Tips to Pick Commercial Surveillance Cameras
As we all know, downtime at the hot-mix asphalt (HMA) plant is unacceptable. If the asphalt operation is quiet, that’s the sound of profit floating away on a fluffy cybercloud of angst.
To keep operations up and running, tech companies such as NordVPN Teams; Irdeto, headquartered in Amsterdam; and Crypto4A, headquartered in Ottawa, Ontario, have introduced secure infrastructure for storing data. “By removing the complex problem of securing assets and services and creating scalable, cost-effective and agile infrastructure, organizations will be able to optimize the way they operate,” Irdeto’s team posited.
Partnering with Crypto4A, Irdeto has released a cybersecurity platform called QxEDGE™ designed for original equipment manufacturers (OEMs) and their operators to deploy and manage sensitive workloads and operations in a secure, digital environment. The product has been introduced to the automotive, rail and construction industries.
Cybertech companies aren’t the only ones working to protect your operations. OEMs and service providers within the asphalt industry—those who know our processes best—have integrated security into the controls and technologies they offer.
For example, the team at Libra Systems Inc., Harleysville, Pennsylvania, a wholly owned subsidiary of Command Alkon, Birmingham, Alabama, provides plant automation, scale ticketing, and business integration solutions for the aggregate, asphalt, and concrete industries. This team suggested encryption standards, such as those recommended by the U.S. Department of Commerce’s National Institute of Standards and Technology (NIST), headquartered in Gaithersburg, Maryland, and the American National Standards Institute (ANSI), headquartered in New York, New York, factor into your plans to safeguard data.
Robert Swartzwelder, chief information security officer for Command Alkon, explained: “Leveraging current industry encryption standards (NIST or ANSI) for your data at-rest and in-transit are foundational to securing sensitive information. The level of difficulty to employ encryption ultimately depends on the knowledge and skill of the technologists engaged in the effort. There are many organizations that specialize in this field if these skills do not exist within the organization.”
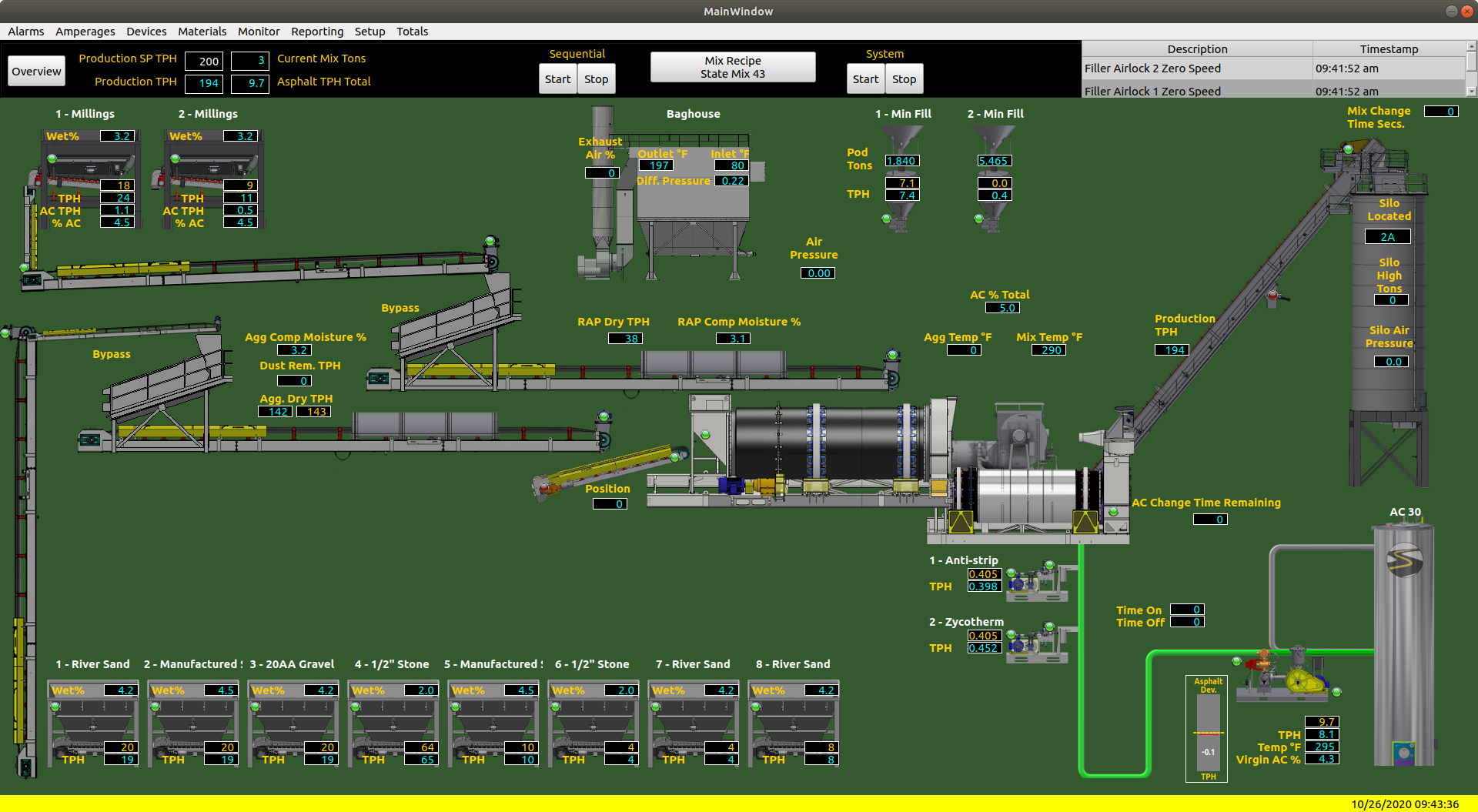
This screenshot shows the Stansteel Accu-Track™ Advantage system. Photo courtesy of Stansteel
In other words, if your asphalt company doesn’t have a specialist who can identify what data to encrypt, and then perform the encryption, find someone who can. Michael Halada, the global product manager automation for Ammann Group, Langenthal, Switzerland, suggested that specialist also be able to build a proper external network for the plant’s VPN. Ammann Group offers the as1 control system for batch or continuous mix HMA plants; it’s designed to run the plant in either manual or automatic modes, provide statistical data to improve the operation of the plant, and back up vital data, among other functions.
“Information like master data for components and recipes/job mix formulae (JMF), is stored in the local database,” Halada explained. “Same is valid for production and operating data as well as the whole configuration parameters for the plant. This data is of high importance and needs to be protected. Therefore, an automatic backup system is available in the as1 system.
“For other systems to connect, the as1 system offers modern REST-based interfaces, which allow data to be collected or transmitted. For remote-accessing the system to edit or create JMF, we usually recommend to use a server or thin client system to which a remote desktop connection can be made. Again, network security is essential here, especially when the remote user is not within the company network. However, as a specialist for control systems, we ask the plant owner to have an external network specialist involved to set up and configure a secured VPN to access the company network.”
REST = representational state transfer; think of it as the platform, rather than the protocol, for data to be shared; it gets its base security from the formatted data
Train Operators for Cybersecurity
Getting a third-party specialist involved in training may be wise, as well. While some elements of safeguarding company information—such as having the CFO password-protect personnel files—look like common sense to information technology (IT) professionals, there are layers of cybersecurity that the average worker might overlook. And there are layers of liability that come into play.
When training plant operators and others who will be handling sensitive company and customer information, don’t be afraid to ask for help. Dan Hughes, the vice president of product management for Astec Industries Inc., Chattanooga, Tennessee, listed help as one of his top four bullet points for training the plant operator to heighten his understanding of cyber criminality. Hughes listed:
- Run anti-virus/security software on all computers within the organization;
- Do not access the public internet from controls computers;
- Create frequent backups to ensure quick recovery in case of a breach; and
- Utilize a third party to periodically test and train on current security threats.
Make sure workers understand what information is sensitive beyond the obvious data stored in the computers. Passwords should be safeguarded, but do employees understand the importance of safeguarding usernames as well? “First of all, use common sense,” Halada reminded us. “Do not communicate given usernames and passwords.”
Look at the amount of time your employees spend with phones in their hands. The 2020 Construction Technology report from JB Knowledge, shows us 93 percent of construction industry workers surveyed used their smartphones for work. Hopefully, they’re not accessing social media to post tonnages for the day and other information that can be mined from poor public relations control. And hopefully they aren’t allowing cybercriminals access to the company portal. Get a handle on that with your robust cybersecurity protocol.
Your smartphone and tablet security can start with something as simple as multi-factor authentication, which most users are probably familiar with. Not only should the device require a username and password for access, it should have a second layer of security before unlocking access. Whether your company requires the employee to provide responses to questions, facial recognition on single-user devices, or another combination of authentication, you want to make it more difficult for criminals who don’t know your operation to “hack into” the system from a remote location.
A handful of controls systems OEMs let down their guard(s) and offered the following tips to beef up your cybersecurity protocol at the plant, quarry or headquarters.
When bringing vendors or customers on-site, don’t give them access to your network.
“Do not allow third-party staff to connect their USB devices to your plant control systems or use the same network,” Halada said. “Do not surf the internet from the plant control system. Do not install any applications onto the plant control system. Use a separate, dedicated personal computer (PC) for email communication and exploring the internet or other business applications. Don’t use the same USB storage disk or stick at business and at home. Make regular backups of the database and relevant data and store it at a safe place.”
Command Alkon/Libra Systems offered similar advice. “Research, identify and then implement a well-rounded cybersecurity training program that meets your organization’s needs,” Swartzwelder recommended. “This is an absolute must.”
The team at PlantDemand, Munich, Germany, recommended training your team to recognize phishing and imposters. “This is the same as in every zombie movie,” they shared. “The most likely way the security will fail is if a human gets tricked into lowering their defenses.”
PlantDemand’s team also recommended your employees learn to rotate their credentials. You may be keeping passwords secret, but you should also change them on a regular basis. Also change certificates and access tokens on a regular basis. Because you should be using systems with change logs, audit logs and backups, you’ll be able to trace who changed what; if necessary, you can undo the changes from a particular user. Each user should have access to only the JMFs, schedules, order fulfillment, accounting information, or other data that he needs, which is all available within “sectors” of the PlantDemand system. Working on the “least privilege principle” could save your business much downtime and angst if there’s a security breach in one area.
While that sounds a little paranoid, take note from NordVPN Teams that as much as 88 percent of data breaches are caused by human error (although only 43 percent of workers admit to having made mistakes that compromised cybersecurity). And note that Verizon recently found 5 percent of data breaches are caused internally. Whether those breaches are accidental or on purpose wasn’t differentiated, but having an officer of your company who can undo mistakes could go a long way toward preventing a problem from snowballing out of control. It’s good housekeeping to mitigate risk by extending cybersecurity and privacy into all business decisions—make it front-of-mind for every employee.
The team from WEM Automation, New Berlin, Wisconsin, listed double-checking the age of your system among your housekeeping items. They reminded readers that Microsoft support for Windows 7 ended Jan. 14, 2020. That means “Microsoft no longer provides updates, security patches or support, making your system more vulnerable to malware, viruses and cyberattacks,” they shared. “If you are still operating with Windows 7, it can become a potential problem.”
The WEM team recommended updating your system(s) to Windows 10 to eliminate exposure to the risks of an outdated system, offering the following tips to minimize risk in the meantime:
- Disconnect your Windows 7 computer from the internet whenever possible;
- Update your browser and discontinue using Internet Explorer;
- Remove any unused software plugins; and
- Only use software that continues to support Windows 7, activate push updates.
For example, the Insignia Control System (ICS) total plant control system from ALmix, Fort Wayne, Indiana, operates on the latest Windows™ platform, according to the manufacturer. It’s designed to control the complete blending process across every plant station and provide real-time plant production data. Among a host of other functions, flexible settings for backup/restore are standard.
Let’s say you’ve kept up with new programs and platforms and are actively training personnel on a robust cybersecurity program. These are excellent steps toward protecting your company’s information. In the asphalt industry, we don’t operate in a vacuum. To put it in over-simplified terms, our environmentally friendly and perpetual pavements are built because we take in liquid, stone, and other material from vendors, create well-planned mixes, and sell the resulting HMA in any of its variations to customers.
All the entities along that supply-and-demand chain deserve a comfort level of cybersecurity as well.

Ensure the rugged phone or tablet used in the field to access or report sensitive data includes robust security measures, such as multi-factor authentication. Photo courtesy of Caterpillar
Get Specific with Customer Access
With many HMA producers electing to give contractors a smoother customer-service experience with electronic ordering and loadout, security comes into play from the very people you want to protect. An asphalt plant manager shared with me that he could track change orders on his phone and see that the plant operator and customer were solving problems in real-time while he ended his day from the comfort of his couch. Mobile apps and remote reporting allow customers—and owners—flexibility and freedom they couldn’t enjoy in the past, but can open networks to hackers if data isn’t safeguarded.
“The modern as1 control system does support interfaces to third-party systems like ERP or even open construction site management platforms like Q Plant from Q Point,” Halada said. “This is used to exchange delivery data, production data, operating data, as well as order information. The communication with cloud-based platforms is using a REST interface over HTTPS with an API Key. Other data is transmitted using MQTT with encrypted data.
“For company internal communication and file transfer, usually both systems are part of an already protected company network (intranet). VPN is used if multiple sites have to communicate with a central server. The control systems usually are behind a firewall, which is configured for special communications ports only.”
Swartzwelder offered this advice to make sure the flexibility you choose works for you: “Cybersecurity is not limited to choosing the important protocols, rather adopting the right security framework for your organizational needs.” He used the example of the Open Web Application Security Project® (OWASP), which is a two-decades-old nonprofit foundation working to improve the security of software. “Following OWASP 10 guidelines, using multi-factor mechanisms with password management, and strong encryption are among the most effective controls to protect transactional data.”
The team at PlantDemand echoed the complex nature of Swartzwelder’s advice, listing a “patchwork of multiple solutions” so providers take care of their infrastructure/different company systems from different locations. While they suggested the VPN require a single sign-on to offer tightly controlled paths and gateways, not all information is in one, easy-to-access place.
Asphalt equipment manufacturers such as Stansteel, Louisville, Kentucky, can offer departmentalized controls with systems such as Accu-Level, Tank Tracker, Tank Manager or NightOwl Advantage Alert System. Or they can integrate the entire system with complete plant controls as comprehensive as the patented Accu-Track™ Advantage.
However you elect to set up your cybersecurity net, OEMs and aftermarket controls providers are taking the criminal landscape into consideration alongside you. It may be a sad reality, but they’re taking cybersecurity into account when designing, installing and training the use of their systems. They can be partners with you in your efforts to increase efficiency and enhance cybersecurity.
The point of asphalt plant controls, connected jobsites, digital data storage and the like is to make construction operations more efficient. The environmentally friendly aspect of reducing paper tickets and blueprints, gas-guzzling trips to and from jobsites, and so on, by digitizing and sharing electronic information is laudable. Our industry should be commended for embracing the efficiencies and sustainability built into the digital workflow. But those efficiencies and sustainability must be safeguarded across the depth and breadth of operations with a mix of common sense and preemptive problem-solving to keep cybercriminals from wreaking havoc on projects and production.
“Cybersecurity is no longer a thing only information security and IT departments care about,” Gurinaviciute said. “As many workplaces rely solely on digital solutions that are used by the entire workforce, staying protected against cyberattacks requires everyone’s joint effort.”
Five Fun Cybersecurity Training Tips
Chief information security officers and training directors teaching the basics of cybersecurity have an uphill battle. Not all construction professionals are aware of the risks to the company’s information or their own. The chief technology officer for NordVPN Teams, Juta Gurinaviciute, explained:
“With the ever-changing and evolving digital threats, maintaining cyber resistance is no longer limited to IT and security officers,” she said. Instead, security depends on every member of the organization. “Constant training is a way to build the team’s resilience against threats.”
Unfortunately, training against computer hackers can be mind-numbing.
Her crew at NordVPN Teams reported: “Those who found training to be very interesting were 13 times more likely to change the way they think about cyber threats and protection against them.”
Here are the five ways her team offered to make cybersecurity training more attractive.
- Gamify it.
Quizzes, games, prizes and quality time with colleagues will enhance enjoyment and learning. Interactive activities boost engagement and yield better results when it comes to cybersecurity teaching.
- Engage in friendly competition.
The key element in gamification is competition; however, putting a prompt question within a video lesson isn’t enough. People are engaged when they have an incentive, be it a prize or pride. Companies could organize periodic competitions to keep a workforce constantly aware of new threats and how to tackle them.
- Make it rewarding.
Turn the right answer into a badge. Give a reward for discovering a vulnerability in the system. Offer a holiday bonus for a year without incident. A reward system is the optimal way to offer the positive feedback people expect while participating in a competition.
- Turn it into a team effort.
Staying protected from breaches and attacks is everyone’s business, thus employees should be encouraged to work in teams. Maybe have them solve riddles with their colleagues; have them craft a phishing email so the team learns together how this criminal technique works and what it looks like.
- Be understood.
The jargon that information security and IT professionals use is a foreign language to the typical plant operator, accountant, paving foreman and so on. When training the whole team, make sure you speak clearly and explain terms in plain language so all the members of the crew understand and remember.
